Running a backend server without public internet access greatly reduces the risk of attacks. In this guide, you will learn how to securely isolate your server while still allowing it to fetch updates, using Leaseweb’s Private Network and a NAT gateway.
Use case
This applies to customers running a backend service, such as a database server, on their Dedicated Server. The goal is to prevent the server from having direct internet access, reduce the risk of malicious attacks and improve overall security.
However, the server must still be able to access the internet to download security patches and updates.
Solution
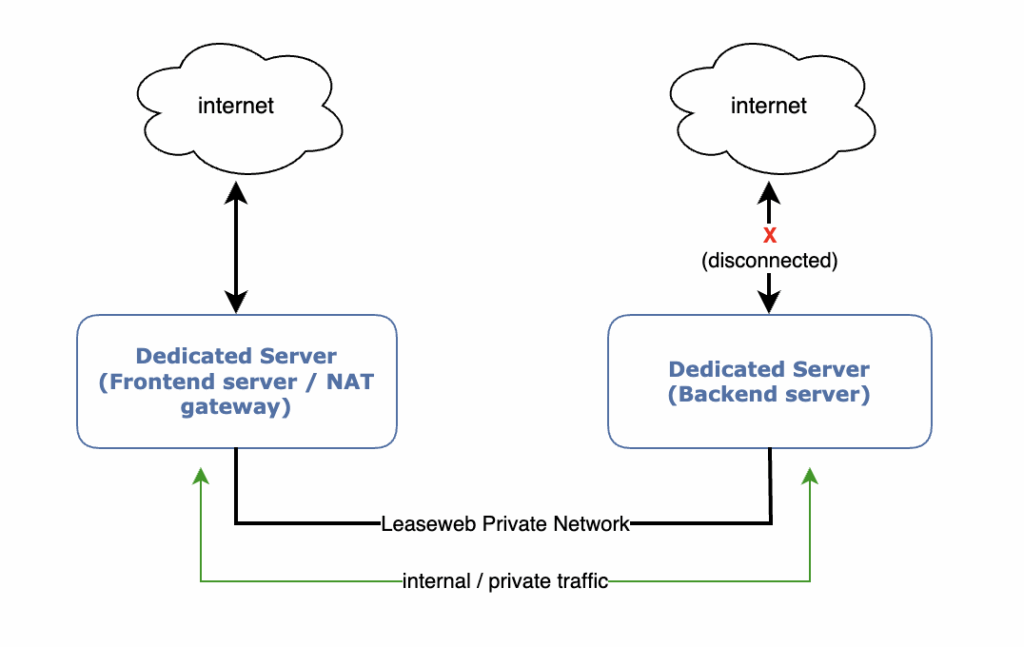
The proposed solution is based on an internet gateway that is used to reach the internet from internal networks.
It assumes the following infrastructure is in place:
- Leaseweb Private Network is attached to the Dedicated Server (backend server)
- A 2nd (Front-end) server is used that has both public connectivity and is connected to the same Private Network as the backend server.
- Or, a firewall appliance or other NAT device (like a Load Balancer) is in place.
By default, Leaseweb delivers each Dedicated server with public connectivity (uplink and a public IP address), which is used to perform an automated install of the Operating System on the server. On the Leaseweb Customer Portal, you can manage the public switch port of the server.
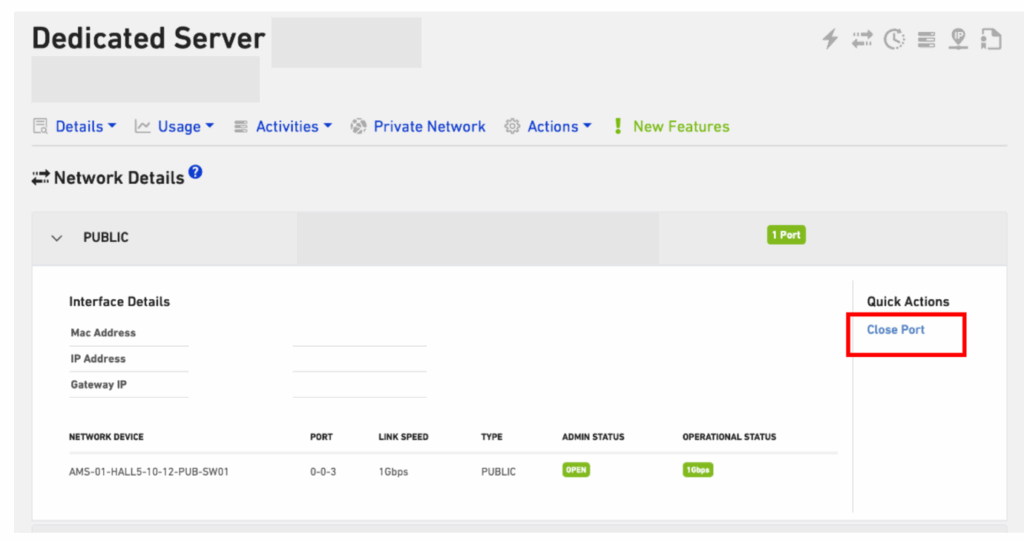
By closing the public switchport, you shut down the public internet connection, but also your direct access to the server. Note that you can always use our Remote Management to gain access to the server’s console.
If your server is connected to a Private Network, you can set your default route (0.0.0.0/0) and default gateway to your frontend server or firewall Private Network IP address.
By doing so, all traffic will no longer use the public NIC but the Private Network.
On your frontend server, which has both internet access and Private Network access (for example, your Webserver), you can configure it as a NAT gateway or use a firewall device that acts as a NAT gateway.
How to configure your server as NAT gateway and set the default gateway
A Linux computer can function as a Network Address Translation (NAT) gateway, allowing a private network to connect to the internet. This is achieved by enabling IP forwarding and configuring NAT rules, typically using iptables or firewall utilities.
Steps to configure a Linux machine as a NAT gateway:
1. Enable IP Forwarding
This allows the Linux machine to forward packets between different network interfaces. You can do this temporarily with :
echo 1 > /proc/sys/net/ipv4/ip_forward
or permanently by modifying the
/proc/sys/net/ipv4/ip_forward setting. 2. Configure NAT Rules
You use iptables to define NAT rules, which map private network addresses to public addresses. For example:
- # Enable NAT (Masquerade) on an outgoing interface
iptables -t nat -A POSTROUTING -o <public_interface> -j MASQUERADE This translates private addresses to the public IP address of the gateway.
3. Configure Firewall Rules
You will need to configure firewall rules to allow the necessary traffic between the private and public networks. For example:
- # Allow forwarding from internal to external
iptables -A FORWARD -i <private_interface> -o <public_interface> -j ACCEPT - # Allow forwarding of established connections back in
iptables -A FORWARD -i <public_interface> -o <private_interface> -m state --state RELATED,ESTABLISHED -j ACCEPT 4. Save and Enable IPTables Rules
If you use iptables, ensure that you save the rules so they persist after a reboot and enable them to run on boot.
5. Set Default Gateway
Configure the clients on the private network to use the Linux machine as their default gateway.
Example Configuration (using iptables):
<public_interface> is eth0 (the interface connected to the internet)
<private_interface> is eth1 (the interface connected to the private network) Here is a simplified example:
# Enable IP forwarding
echo 1 > /proc/sys/net/ipv4/ip_forward
# NAT rules
iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
# Firewall rules (forwarding traffic)
iptables -A FORWARD -i eth1 -o eth0 -j ACCEPT
iptables -A FORWARD -i eth0 -o eth1 -m state --state RELATED,ESTABLISHED -j ACCEPT
# Firewall rules (accept incoming traffic)
iptables -A INPUT -i eth0 -j ACCEPT
# Save iptables (if needed)
# iptables-save > /etc/iptables/rules.v4 Important Considerations
- Security: Carefully configure your firewall rules to prevent unauthorised access.
- IP Address: Ensure that the Linux machine has a public IP address assigned to the public interface.
- DNS: Configure DNS on the private network so devices can resolve domain names to IP addresses.
With a NAT gateway and private routing, your backend server stays secure and off the public internet, without losing access to essential updates – a simple setup with a strong impact.