This article provides insights into filtering API allowed IP addresses for Kubeconfig access and managing your Kubernetes cluster. Limiting access to trusted API IP addresses reduces the risk of malicious attacks and ensures that only authorised personnel can control the cluster.
The list of IP addresses to use depends heavily on where the personnel are accessing the cluster from. Refer to your company’s IT department to know which addresses to use.
Applying IP restrictions to limit who can manage your cluster
- In the Leaseweb Customer Portal, go to the “Kubernetes” tab
- Select the cluster you want to protect and click the cluster ID button
- The loaded page allows you to customise your cluster. Navigate to the “Kubernetes API Allowed IPs” in the Security section
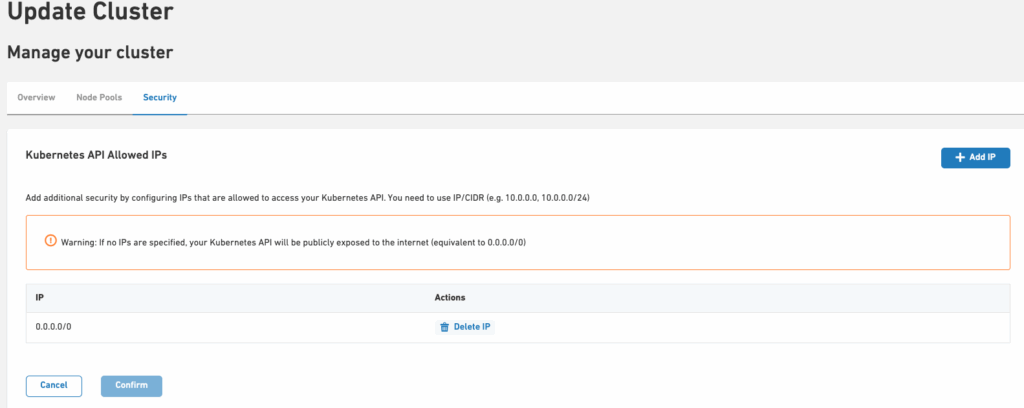
Warning
By leaving the list empty, or by specifying 0.0.0.0/0 you are effectively letting anyone with a valid token manage your cluster, which is not a safe way to secure your cluster.
- Use the “Add IP” button to add a new IP address to authorise the management of your cluster
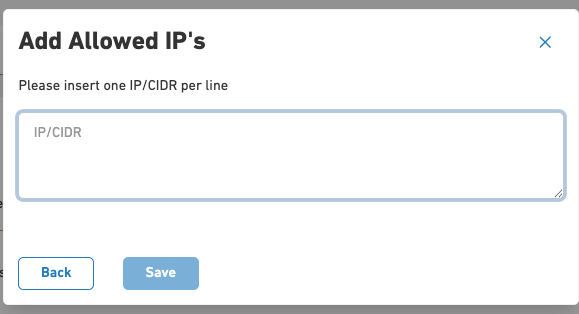
- Remove any undesired IP using the “Delete IP” button
- You will be asked to confirm that you indeed want to remove that IP
- Keeping obsolete IPs away from the authorised IP list and reviewing the list periodically can help enhance your security!
- At the bottom of the page, confirm the changes using the “Confirm” button
- The changes will be applied to your cluster in a couple of seconds.
Once these changes are applied, only users using one of the specified IP addresses will be able to manage this cluster.
You can also view the allowed IPs for each cluster on the cluster’s main page by clicking the “View Allowed IPs” option.
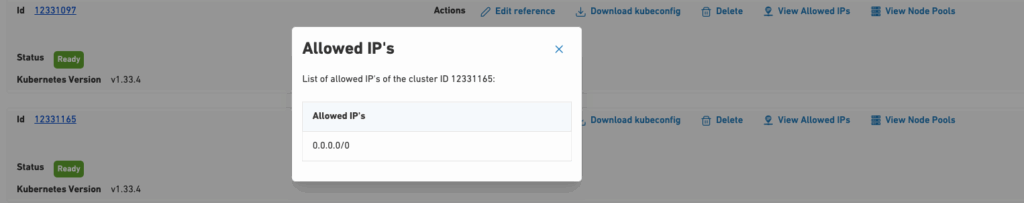
Information
Ensure that you regularly review these IP addresses to confirm they are the ones administrators commonly use to connect to your clusters.